Security and Compliance
Enterprise-Grade Security for Your Business
Your trust is our priority. We maintain the highest standards of security and compliance to protect your business data.

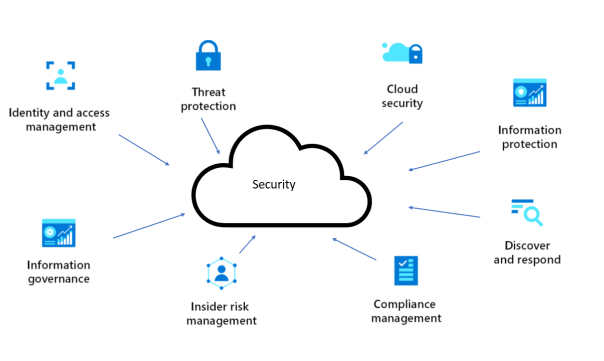
Security Overview
Multi-Layered Security Architecture
Contact Methods
- Bank-level 256-bit encryption
- Multi-factor authentication (MFA)
- Real-time fraud monitoring
- Continuous security testing
- Regular penetration testing
- 24/7 security operations center
Data Protection
Protecting Your Business Data at Every Level
Infrastructure Security
- AWS and Google Cloud infrastructure
- Redundant data centers
- Real-time data backup
- Disaster recovery protocols
- 99.99% uptime guarantee
Data-Driven Approvals
- Data encrypted in transit and at rest
- Secure SSL/TLS connections
- Encrypted database systems
- Secure key management
Flexible Financing
- Role-based access control
- IP address restrictions
- Regular access reviews
- Automated session timeouts
- Strict password policies
Our Values
Meeting Global Security Standards
Infrastructure Security
- AWS and Google Cloud infrastructure
- Redundant data centers
- Real-time data backup
- Disaster recovery protocols
- 99.99% uptime guarantee
Infrastructure Security
- AWS and Google Cloud infrastructure
- Redundant data centers
- Real-time data backup
- Disaster recovery protocols
- 99.99% uptime guarantee

Additional Information
Security Resources
Available Resources
- Security whitepaper
- Compliance certificates
- Privacy policy
- Security FAQs
- Best practices guide
Operational Security
Security in Every Operation
Personnel Security
- Background checks for all employees
- Regular security training
- Security awareness programs
- Clear security protocols
- Signed confidentiality agreements
Vendor Management
- Strict vendor vetting process
- Regular vendor assessments
- Security requirements in contracts
- Ongoing monitoring
Prepared for Any Situation
Incident Response
Response Protocol
- 24/7 incident response team
- Documented response procedures
- Regular incident response drills
- Client notification protocols
- Post-incident analysis
Integration Security
Secure Third-Party Connections
Integration Protection
- Secure API connections
- OAuth 2.0 implementation
- Regular security reviews
- Monitored integrations
- Secure credential storage
Meeting Global Standards
Regulatory Compliance
Key Regulations
- Financial services regulations
- Data protection laws
- Privacy regulations
- Industry standards
- Local requirements
Monitoring & Testing
Continuous Security Verification
Security Operations
- 24/7 system monitoring
- Automated threat detection
- Regular vulnerability scans
- Penetration testing
- Security log analysis
Security in Your Hands
Client Controls
Available Controls
- Custom access permissions
- Activity audit logs
- IP whitelisting options
- Custom security policies
- Integration management
Trust Center
Transparency Builds Trust
Status Updates
- System status page
- Security advisories
- Maintenance schedules
- Incident reports
- Update notifications

Trust Center
Transparency Builds Trust
Infrastructure Security
- System status page
- Security advisories
- Maintenance schedules
- Incident reports
- Update notifications
